For the first time in history, banks and financial institutions are adopting digital assets as an integral part of their internal operations and product offerings. As they do so, they face new threat vectors, unfamiliar custody models, and growing pressure to identify and align with emerging supervisory standards, which may or may not serve as complete safe havens from risk. Global regulators are stepping in to lay the groundwork for formal digital asset frameworks that codify recognized best practices, but technical specifics around custody architecture remain unevenly defined at this early stage.
At Fireblocks, we have developed a custody technology framework to help bridge that gap. Designed to support regulated institutions, this framework is an opportunity to align best-in-class infrastructure with supervisory expectations and operational best practices, offering a practical, repeatable model for secure, scalable digital asset custody.
The following diagram and text provide an overview of the structured approach we have used in the custody technology framework. Among other things, it addresses the critical domains of risk management, control enforcement, and governance that institutions should move to operationalize today.
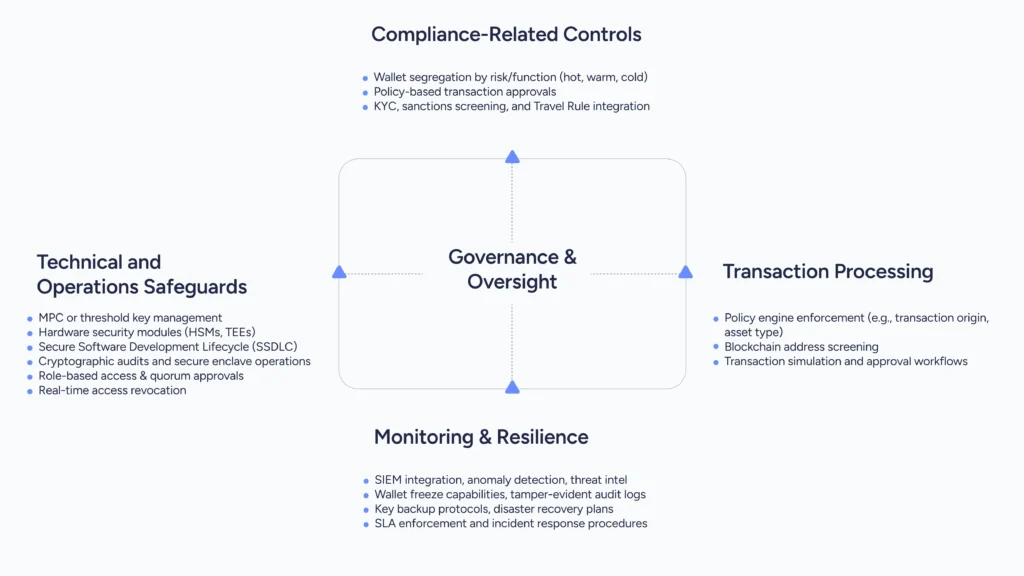
As illustrated above, this multi-layered supervisory risk framework for digital asset custody is structured across four core domains:
- Compliance-related controls
- Technical safeguards,
- Transaction processing
- Monitoring and resilience
This framework aligns with NIST CSF 2.0 and global regulatory expectations, providing a model for banks to operationalize custody governance.
How do our recommendations in these categories compare with traditional models? To set the context, it is helpful to understand how supervisory expectations for digital asset custody operations diverge (or should diverge) from those applied to traditional financial infrastructure.
Comparing Traditional and Digital Asset Compliance
Across jurisdictions, regulators are extending traditional control expectations around access, segregation, incident response, and auditability into blockchain-based operating environments. The table below highlights key distinctions between traditional and digital asset compliance frameworks in these important areas, illustrating how baseline obligations are being adapted to reflect cryptographic infrastructure and real-time operational risk.
Chart: Traditional vs. Digital Asset Risk Management
| CATEGORY | TRADITIONAL FINANCE | DIGITAL ASSETS |
| Custody model | Custodian holds and controls customer assets and access | Asset owner holds, manages and controls assets via programmable infrastructure (key distribution) |
| Governance & Risk Controls | Periodic audits, static role definitions, and manual approvals | Real-time monitoring, automated policy enforcement, role-based access with quorum and revocation logic |
Technology Risk Expectations | General cybersecurity requirements, e.g., for IT systems, third party vendors | Cryptographic key management, secure enclave operations, threshold signatures, and onchain transaction processing |
Third-Party Oversight | Structured third-party risk management through certifications, audits, and regulatory review | Bespoke or evolving standards for custody activities (e.g., key backup) and smart contract audits) on top of standard third-party expectations applied to a range of vendors across system boundary of cryptographic activities |
These contrasts reflect a shift in how bank decision-makers and risk managers define, measure, and manage within digital assets activities. The next phase of regulatory development, risk alignment, and strategic implementation will require institutions to internalize new supervisory baselines while positioning compliance as a key operational component.
Core Risk Management Domains
As supervisory expectations begin to formalize, institutions will be evaluated not only on policy alignment, but on the degree to which controls are embedded across custody operations. Risk management in this context is not abstract. It is defined through specific domains where auditability, governance, and technical enforcement must intersect:
- Compliance-related controls
- Technical and operations safeguards
- Transaction processing
- Monitoring and resilience
Compliance-Related Controls
Institutions must ensure that their digital asset custody architecture includes compliance-related controls that address traditional regulatory requirements while also addressing specific risks unique to blockchain-based activity. Key considerations include transaction monitoring, sanctions screening, know-your-customer (KYC) and counterparty due diligence, and Travel Rule implementation.
Digital asset custody introduces new operational elements that allow for tailored compliance capabilities, such as address whitelisting, integration with blockchain intelligence tools, and policy-based transaction approvals. A defensible compliance posture requires institutions to define and enforce access privileges across all wallet operations and transaction workflows. Relevant considerations include configuring transaction approval processes that enforce real-time policy checks—based on parameters such as wallet origin, destination, and transaction volume—and tying these controls to identity verification and user roles.
These controls must function across both custodial and transaction workflows, with tamper-evident audit logs and real-time alerting to support internal investigations and supervisory requests.
Technical and Operations Safeguards
Technical infrastructure must reflect a defense-in-depth architecture specific to digital asset risks. Such software and hardware include cryptographic key management using distributed generation techniques (such as MPC or threshold signatures), secure enclave-based transaction signing, and layered access controls.
Wallet architectures should consider the specific business model to tailor configurations (e.g., omnibus versus segregated structures), with permissions and access controls mapped as appropriate (e.g., by asset class, user role, or function). Institutions should be able to revoke access privileges in real time, ensure role-based governance across operational teams, and demonstrate how these capabilities reduce the risk of unauthorized access or insider threats.
Institutions should also conduct end-to-end testing of the above, including via cryptographic audits, by enforcing SSDLC standards, and by testing resilience through regular red-teaming exercises.
Transaction Processing
Compliance enforcement must be embedded directly into transaction workflows. This includes programmable policy engines that control transaction approvals based on wallet origin, risk tier, and asset type, and transaction size or frequency. [add other reasons for a policy engine]. Blockchain integrations now support address screening, deny-list enforcement, and transaction simulation before execution. These safeguards ensure that processing logic aligns with both institutional policies and jurisdiction-specific obligations.
In onchain environments, institutions must also account for risks that differ from traditional infrastructure, including malicious smart contracts and execution-level threats. These considerations may require business model-specific workflows, such as transaction simulation before execution, multi-step approval routing, or custom rule sets that extend beyond traditional finance controls. Collectively, these safeguards ensure that processing logic aligns with institutional policy and jurisdiction-specific regulatory obligations.
Monitoring and Resilience
As expectations shift from periodic audits to continuous assurance, institutions must demonstrate real-time visibility, threat detection, and incident response capabilities. Governance frameworks must define uptime targets, incident escalation protocols, and contingency measures for wallet infrastructure and third-party providers. These controls should extend across transaction layers integrated with SIEM systems, alerting mechanisms, and anomaly detection tools.
Operational resilience also includes evidence-based recovery planning. Institutions must maintain key backup protocols, enforce SLAs with infrastructure partners, and demonstrate the ability to freeze wallet activity and preserve data integrity in response to threats. Supervisory priorities are moving toward demonstrable uptime performance, immutable audit trails, and verified enforcement of system-level safeguards.
Compliance as Institutional Infrastructure
As regulatory frameworks for digital assets continue to evolve, institutions are under pressure to operationalize compliance in a way that meets both supervisory expectations and internal risk standards. While global regimes vary, foundational principles are converging around areas like cybersecurity, governance, and operational resilience. Frameworks such as DORA in the EU and NIST CSF 2.0 in the United States provide institutions with a strong starting point for aligning their custody operations with regulatory priorities.
The model presented here is Fireblocks’ articulation of a custody technology framework for regulated institutions. It translates emerging regulatory principles into practical infrastructure design, offering a structured approach to embedding compliance into custody architecture. By building controls directly into technical systems, institutions can improve auditability, mitigate risk, and prepare for formal rulemaking.
This shift presents an opportunity. When designed and embedded as infrastructure, compliance becomes a strategic advantage. It supports product development and scaling defined within the bank’s risk appetites, supports entry into regulated markets, and establishes the operational integrity required to scale with trust.
FAQ
-
What is digital asset custody in banking?
Digital asset custody refers to how banks manage and secure tokenized assets and cryptocurrencies. In a direct custody model, institutions maintain control over private keys using secure wallet infrastructure instead of relying on third-party custodians. -
What is direct custody and why is it important for banks?
Direct custody is a custody model, only possible in digital asset contexts, that gives banks and non-bank corporates complete control over digital assets and operations without introducing counterparty risk. It ensures assets remain off the custodian’s balance sheet and are protected using institutional-grade wallet infrastructure like MPC-CMP. -
How do institutional wallets enable secure digital asset custody?
Institutional wallets are designed to meet the needs of regulated entities and non-regulated corporates. They use MPC, role-based access, programmable controls, and tamper-proof audit trails to support secure, compliant operations at scale. -
How is digital asset custody different from traditional asset custody?
Traditional custody relies on custodians holding customer assets. Digital asset custody enables direct or delegated control through blockchain infrastructure. Risk management is embedded through real-time policy enforcement, cryptographic controls, and auditability. -
What is MPC technology and why is it used for digital asset security?
MPC (Multi-Party Computation) technology distributes transaction signing across multiple devices, removing single points of failure. It’s used to enhance wallet security, enforce internal controls, and support institutional-grade digital asset infrastructure. -
Why do banks need a risk framework for digital asset custody?
As banks enter digital asset markets, regulators expect them to implement governance frameworks that align with standards like NIST CSF 2.0 or DORA. A structured risk framework ensures operational resilience, compliance, and scalability. -
What compliance controls are essential for digital asset custody?
Banks must implement real-time controls like sanctions screening, transaction monitoring, Travel Rule compliance, and address whitelisting. These controls must be auditable and enforceable across both operational and transaction layers. -
How do banks detect threats in digital asset custody environments?
Effective digital asset custody includes real-time monitoring, anomaly detection, and automated alerts. These capabilities integrate with SIEM systems and incident response workflows to ensure continuous protection and auditability.


