The rise in cyberattacks on crypto platforms—most recently the Bybit breach—has exposed alarming vulnerabilities across the industry. This report delves into the evolving landscape of crypto security, highlighting new challenges and advanced guidance for safeguarding digital assets in this new era.
Section 1: The Perfect Storm – Market Acceleration, Advanced Use Cases, and New Risks
The crypto and digital asset industry stands at a turning point. With institutions like BlackRock introducing Bitcoin ETFs, the tokenization of Real-World Assets (RWAs) gaining traction, and payment innovation continuing to grow with stablecoin transactions, the market is quickly evolving.
At the end of 2024, the total market capitalization stands at $3.2 trillion, DeFi’s total value locked (TVL) has returned to its 2021 peak at $134 billion, and the combined market value of USDT and USDC exceeds $204 billion.
New conditions and continued efforts by hacker groups such as Lazarus introduce dizzyingly complex attack vectors — including API exploits, advanced insider threats, and exploits of different blockchain configurations. Though private key security and traditional protection against transfer of funds are still important, relying on security solutions of years past is insufficient.
Meanwhile, more users, more funds, and more transactions create larger targets for attackers.

Why Attacks are Increasing
1. Higher Transaction Volumes
As blockchain transactions increase, so do potential targets for attacks and financial incentives for attackers.
2. Surge in Users & Wallets
With more individual and institutional users, each new wallet or account is a potential entry point for attackers, expanding the attack surface.
The global cryptocurrency user base expanded by nearly 40 million in the latter half of 2024.
Source: Most In-demand Web3 Jobs of 2025
3. More dApp Interactions
dApps introduce vulnerabilities via smart contracts and potential front-end attacks, with users at risk of phishing and developers facing bugs or improper access to admin functions.
4. Growing Personnel Needs
As crypto adoption rises, so does the need for qualified staff. Under-resourced organizations risk human errors, insider threats, and malicious fake candidates. This is amplified with fully-remote engineering positions.
The Web3 job market has seen a 45% increase in job postings year-over-year.
Source: Most In-demand Web3 Jobs of 2025
5. Expanding API Usage
APIs are critical for the fast and automated delivery of crypto services, but poor design or lack of security can expose sensitive systems to cyberattacks.
6. Entry of New Market Players
New players bring innovation but also unfamiliar risks, often becoming targets due to weaker security practices and working knowledge of the industry.
7. More Blockchains & Implementations
The growth of different blockchains increases the attack surface, with each protocol having unique vulnerabilities.
8. Expanding Use Cases & Features
New blockchain features like smart contract wallets and AI agents introduce new security risks, as more complex systems provide more opportunities for attackers.
9. AI in the wrong hands
AI is enabling attackers to automate and scale sophisticated exploits that deceive users through deepfake social engineering and advanced phishing, leading to significant financial losses from unauthorized transactions.
Section 2: Legacy Security Won’t Protect the Next Billion Users
Unlike traditional cyber attacks that focus on indirect monetization through data theft or ransom, crypto-related attacks focus on direct monetization by compromising the business logic of financial applications and operational workflows, allowing attackers to access financial transactions. We see three critical areas of security vulnerabilities in the industry today that need to be addressed before onboarding the next billion users.
1. Centralized Exchanges and Retail Applications: The Frontline of Attacks
Centralized exchanges and retail applications serve as the primary gateway to crypto for both retail users and institutions. Because of this, centralized exchanges are primary targets of attackers because: (1) they hold hundreds of millions or billions of assets under custody (AUC), often concentrated into omnibus accounts; (2) they represent a wide attack surface, from end-user vulnerabilities to a sizable operation, tech and support employee base subject to insider threats – all subject both on-chain and off-chain vulnerabilities.
Real-Life Attack: Bybit’s $1.5B hack occurred when Lazarus compromised a Safe{Wallet} developer’s machine, gained access to its production environment, and deploy malicious code directly into Bybit’s wallet UI. This allowed them to manipulate Bybit’s transaction, which Bybit unknowingly approved through blind signing using Ledger devices, ultimately transferring $1.5B to Lazarus’ address.
State actors and groups supported by them, like the Lazarus group, are formidable adversaries. We have little to no margin for error and have to stay on our top game all the time.
Key Areas of Vulnerability & Attack Vectors
Given the wide range of potential attack points, crypto organizations must be aware of where their vulnerabilities lie. Below are the key areas of vulnerability in both the end-user and organizational layers.
| End User | Phishing Attacks: Tricking end users to sign malicious transactions, reveal private keys or login credentials. Both simple and advanced AI methods create more sophisticated and convincing attacks. Address Poisoning: Attackers modify or poison wallet addresses in transaction data, sometimes masked by UI manipulation, redirecting funds to malicious addresses. |
| Organizational | Personnel & Hiring: Attacking the Weakest Link Phishing & spear phishing – Phishing attacks, including more targeted spear-phishing attempts, often focus on stealing credentials, gaining development access, or compromising email accounts to manipulate transactions directly. Malicious Insider – Insiders with authorized access can be a major threat, either acting maliciously, and facilitating security breaches. Fake Recruiting – Attackers impersonate recruitment firms or organizations, tricking key personnel into executing malicious code as part of a fake coding exercise. Fake Candidates – In some cases, attackers apply for positions within an organization, only to gain access and launch attacks once hired. This is amplified with fully-remote engineering positions. API-Based Automation API-exploits aimed at stealing credentials to gain access to critical crypto-related operational workflow systems abuse the trust in machine-based transaction management. Operational Workflows: exploiting weaknesses in internal processes Blind Signing Exploits – Attackers leverage a mispurposed security architecture of separate wallet and key management approval systems to manipulate a transaction and exploit a blind signing practice. Fake Deposit Attack – Attackers exploit weaknesses in how exchanges credit user balances before finalizing a deposit, with partially-completed or unconfirmed transactions, or ownership confusion over deposit transactions. Private Key Exploits – Exploits targeting key management systems (KMS), stealing private keys and draining centralized wallets. Supply Chain Attacks – Attackers compromise third-party vendors or contractors with access to an organization’s internal systems. |
Real-Life Attack:
A DeFi protocol’s Twitter account was compromised and used to promote a fake token launch. This deceived a portfolio manager at an asset management firm into connecting their account to a phishing dApp and ultimately signing a malicious Permit2 transaction, unknowingly granting the attacker an allowance over the firm’s assets. This off-chain approval gave attackers control over the firm’s assets, allowing them to drain funds in a follow-up transaction—resulting in a seven-figure loss.
2. Transaction & Access Policies: Table Stakes for Defense
An attacker’s primary goal is to gain control of funds. Highly integrated and complex operations get risky, particularly as they pertain to core treasury operations, token issuance & lifecycle management & DeFi and Web3 Operations.
Transaction and access policies are a central defense mechanism, creating clear boundaries that dramatically reduce the “blast radius” of an attack. However, the challenge lies in crafting policies that strike a balance between strict security and operational efficiency, ensuring both protection and agility. Even more foundational is the need to ensure the underlying system’s integrity to avoid the policy engine itself from being breached, manipulated, and therefore bypassed.
Real-Life Attack:
A hacker exploited a centralized exchange by using a multi-step fake deposit attack. The attacker used a mule to pass KYC on a new account, and generated a deposit address directly linked to their account. A malicious smart contract was set up to only partially complete a transaction – ultimately deceiving the exchange’s infrastructure into crediting funds that were never actually transferred. The attacker built up a fake balance worth hundreds of thousands, and gradually withdrew real funds from the exchange’s hot wallet.
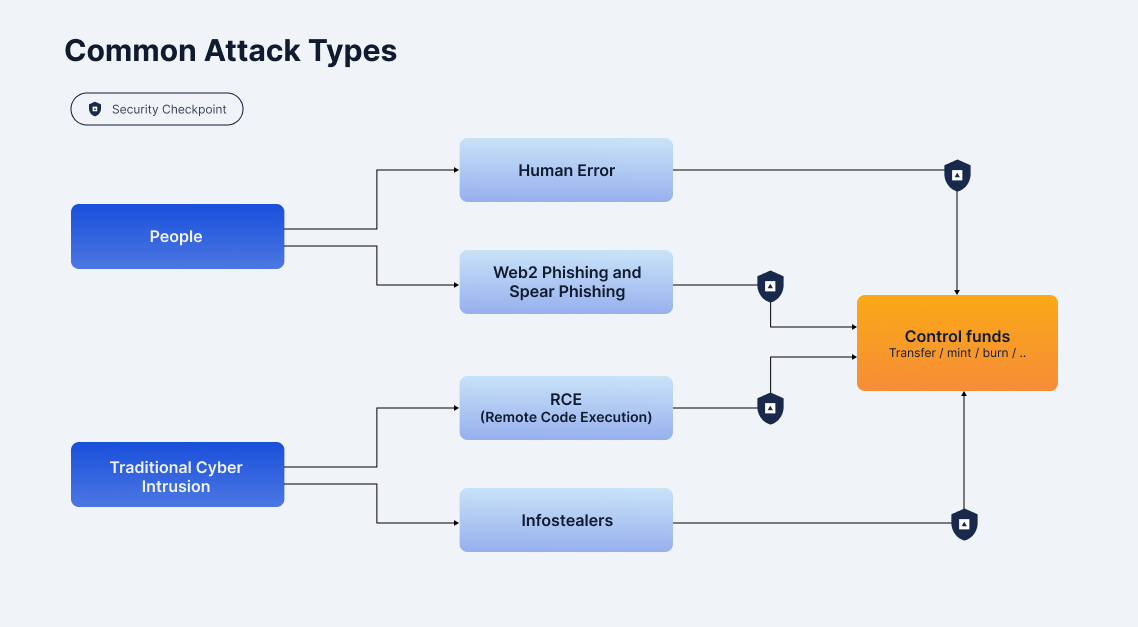
Common Attack Types
The attack surface is focused on three specific areas: (1) Core Treasury Operations; (2) Token Issuance & Lifecycle Management; (3) DeFi & Web3 Operations. Insider threats, such as malicious actions or negligence from employees or contractors, can lead to severe damage if not properly managed. Additionally, both traditional and advanced phishing techniques, such as Web2 phishing and Web3/Ice phishing, remain prevalent, putting sensitive credentials and decentralized systems at risk. Understanding and addressing these threats is crucial to safeguarding both centralized and decentralized systems from malicious activities.
- Insider Threats: Employees or contractors with access to sensitive systems can be a significant security risk. Insider threats can range from malicious actions to negligence, both of which can result in significant damage if not managed properly.
- Web2 Phishing: Traditional phishing attacks are still a major threat in the crypto space. These often lead to credential theft, enabling attackers to gain unauthorized access to user accounts and systems, and sometimes even facilitating machine takeover.
- Web3/Ice Phishing: This advanced form of phishing targets the decentralized aspects of crypto, such as wallet interactions and smart contracts. In the crypto-native version of traditional phishing, attackers would trick users into signing malicious transactions such as permits in order to gain control over user’s funds.
- Address Poisoning: This attack technique involves tricking users into sending funds to an attacker-controlled address by “poisoning” user’s transaction history with similar-looking addresses. They generate many addresses that look similar to common counterparties of the target wallet, interact with the target, hoping the victim would send funds back altering or “poisoning” addresses in transaction data.
3. APIs: The Key to Scaling Securely—or Risking It All
API-based automation is becoming essential for high-throughput to efficiently scale and meet growing user demands. However, this also introduces vulnerabilities. Specifically, API keys tokens and machine access tokens are attractive targets to attackers as they offer a direct path to financial theft, usually bypassing traditional approval processes. As API automation grows, implementing a strong policy-based framework for API management is crucial to mitigate potential security risks.
Common Attack Types
People:
- Human Error: Employees or contractors who manage API keys are often the weak link. Improper handling of API keys, such as storing them in public code repositories or using weak configurations, opens up easy avenues for attackers to steal or misuse the keys. Simple mistakes in key management can lead to severe security breaches.
- Web2 Phishing & Spear Phishing: Attackers may use phishing tactics to gain access to network systems, including tricking employees into revealing API keys or credentials. Spear-phishing, a more targeted approach, focuses on specific individuals to gain deeper access to the organization’s infrastructure and APIs.
Traditional Cyber Intrusion:
- RCE (Remote Code Execution): Attackers can exploit vulnerabilities in the system to execute remote code, gaining access to mission-critical internal systems. Once inside, they can steal or manipulate API keys to carry out malicious actions.
- Infostealers: Malware designed to capture sensitive information can be used to harvest API keys from compromised system.
Section 3: 8 Advanced Tips for Securing your Crypto Security Operations in 2025
1. Craft an end-to-end security architecture, ensuring secure checkpoints at every step of the way
Secure-by-design architecture, robust policy & governance controls, integrated yet sophisticated multi-device approval, real-time transaction visibility and automated threat detection help prevent blind signing and hidden exploits.
2. Map and monitor all external infrastructure dependencies
For all external infrastructure systems, your team will utilize, like smart contracts, oracles or even external vendors, keep close track of dependencies and vulnerabilities, both on- and off-chain, always waiting for community validation before deploying updates.
3. Strictly define and enforce your wallet policies
Implement transaction authorization policies to define security guardrails based on your business’ logic and threat modeling. Ensure that critical and/or sensitive operations are properly escalated to the appropriate approvers.
4. Access Control
Minimize risk exposure by setting up role-based permissions to control access to sensitive financial operations, smart contract deployments, and other key systems.
- Minimize administrative privileges and require multi-step approval for all major changes.
- Define strict smart contract access based on organizational roles and responsibilities.
- Revoke access for departing employees and monitor inactive accounts to ensure principle of least privilege.
5. Contract Whitelisting & Permissions
Limit interactions to pre-approved destinations and trusted contracts, and ensure that whitelisting of new addresses goes through senior staff – enabling the rest of the organization to work efficiently within these boundaries.
6. Secure API-based Automation
- Limit API users permissions strictly to their purpose
- Rotate API keys regularly .
- Enable IP whitelisting for APIs to restrict access.
- Implement monitoring for suspicious activity outside of the service’s responsibilities
7. Audit Code Regularly
Audit both on-chain and off-chain code to maintain robust security and avoid business-specific as well as generic vulnerabilities in your code. Vulnerabilities in either can lead to serious consequences. Use reputable audit firms and continuous testing to stay ahead of potential exploits.
8. Develop an incident response plan
Be prepared and ensure security is up to date as your business changes. Conduct quarterly operational and system tests from the ground up. Identify permission weak points, system vulnerabilities, and governance logic gaps. Continuous improvement is where you stay ahead of adversaries.
Crypto adoption is growing rapidly, and with it, the scope of security threats continues to expand. As the next wave of users comes on-chain, it’s crucial that your organization remains proactive, vigilant, and adaptable with the most advanced intelligence and practices in hand to handle the threats that lie ahead.