The most effective social engineering campaigns don’t rely on obvious red flags or technical exploits. They move through familiar business interactions, like hiring conversations, project discussions, and routine follow-ups that are designed to feel legitimate from the start.
Fireblocks Security Research recently identified a recruiting impersonation campaign targeting tech workers that closely resembled a legitimate Fireblocks hiring process. Questions from job seekers about a project Fireblocks was supposedly hiring for prompted our investigation, which uncovered a broader, coordinated effort by malicious actors.
Further investigation showed a structured social engineering operation using a fake hiring flow to deliver malware disguised as a coding assignment. The tradecraft and execution closely matched a well-established spear phishing, social engineering, and malware pattern attributed to the North Korean “Lazarus Group” (APT 38)-linked threat actors and matching campaign techniques commonly referred to as “Contagious Interview.”
Examining how this campaign unfolded provides a concrete view into that threat pattern in practice. We’re sharing this to help the broader business community stay vigilant and recognize similar activity before others are caught out.
We have also published an in-depth technical malware analysis that provides a detailed breakdown of the campaign’s infrastructure, malware behavior, and indicators of compromise (IOCs).
How the Crypto Job Scam Worked: A Social Engineering Campaign Targeting Tech Workers
This multi-phase campaign highlights how fake crypto recruiter scams have evolved to use developer workflows, like GitHub cloning, to deliver malware targeting digital asset environments.
Phase 1: Initial Contact
People were approached on LinkedIn by individuals presenting themselves as Fireblocks executives, recruiters, or hiring managers. The profiles appeared credible, with realistic work histories, profile photos, and extensive networks aligned with technical and blockchain roles.
Phase 2: Trust Building
Once contact was established, candidates were sent clean, professionally-formatted PDF documents (for example, “Fireblocks.pdf” or “Fireblocks-hiring.pdf”) describing a fictitious project presented as part of the hiring process. These documents included references to a specific product concept, were supported by an extremely detailed Figma board to reinforce legitimacy, and did not include the usual typos and grammatical errors we often see in phishing emails.

Conversations at this stage were professional and detailed, covering role expectations, scope of work, and compensation, culminating in the scheduling of a video interview with an individual presented as the hiring manager.
Phase 3: Video Interview
The interview was conducted via Google Meet and presented as a formal step in the hiring process. The interviewer introduced themselves as an “HR Manager” and conducted the conversation in a professional manner consistent with legitimate recruiting interviews, with questions about the candidate’s professional experience, compensation expectations, and more.
The interviewer ended the call with a code review task as part of a “Fireblocks Poker Platform” project as the next step in the process and shared a link to the repository associated with the assignment. After sharing these details, the interviewer abruptly ended the call, typically citing another scheduled meeting as the reason for leaving.
Phase 4: Malware Delivery
In a pattern consistent with other developer-focused malware threats in the blockchain industry, candidates were instructed to clone a GitHub repository and run standard setup commands, including npm install as part of the assigned code review task. These steps, typical in legitimate developer workflows, triggered the execution of malicious code.
The campaign also employed EtherHiding, a novel technique that leverages blockchain smart contracts to host and retrieve command-and-control infrastructure, making the malicious payload more resilient to takedowns.
These steps triggered the execution of malicious code hidden within the project. Running the setup process resulted in malware being downloaded and executed on the victim’s system, giving the attackers a foothold in the victim’s machine.
Indicators of a Contagious Interview–Style Campaign
Taken together, the structure of the hiring flow, the staged recruiting materials, and the malware delivery mechanism matched characteristics Fireblocks has previously observed in campaigns attributed to North Korean threat actors. The activity is closely aligned with a well-established spear phishing and social engineering pattern commonly referred to as Contagious Interview.
Our investigation also revealed linkage to a previous recruitment-focused campaign impersonating the Multibank Group, which used a similar fake cryptocurrency poker platform as part of its lure. In this case, the same core approach appeared again, but with more detailed artifacts, broader impersonation, and a more capable technical execution, indicating an evolved and more potent iteration of a known campaign pattern.
The following key indicators were central to us identifying the campaign as a textbook Contagious Interview attack:
| Red flag observed | How it appeared in this campaign |
| Requests to clone GitHub repositories and run installations | During the interview, candidates assigned tasks with instructions to clone a GitHub repository and run setup commands (including npm install) as part of a code review task |
| Video interviews that end abruptly once technical tasks assigned | Google Meet interviews ended unexpectedly after a code review task was assigned, with the interviewer claiming they had another meeting |
| Personal email addresses used for corporate recruitment | Recruiter personas communicated using personal email accounts rather than Fireblocks domains (e.g., [email protected]) |
| Calendly links on personal domains | Interview scheduling links pointed to personal Calendly pages not associated with Fireblocks-controlled domains |
| AI-generated profile content with excessive buzzwords | LinkedIn profiles contained generic, buzzword-heavy “About” sections obviously written by AI, use of stock photos |
| LinkedIn recruiter profiles with little prior activity suddenly becoming active | Profiles showed minimal historical activity in time period before contact |
| Reconnaissance-type questions during interviews | Interviewers asked candidates about cryptocurrency payment preferences as part of the interview conversation |
What are These Recruitment Scams After?
The objective of Contagious Interview–style campaigns is financial theft, achieved by gaining access to credentials, authentication material, and environments that can be leveraged for follow-on activity.
At the individual level, executing malicious code as part of a staged hiring assignment can expose personal credentials, development environments, and sensitive information, including private keys and seed phrases that can be used to steal digital assets. The risk does not stop there.
When these tasks are completed on company-managed devices or within corporate development environments, attackers gain a potential foothold into organizational systems.
This is why fake recruiting campaigns aimed at developers and engineers are such an effective lure. Hiring workflows provide a legitimate pretext for cloning repositories, installing dependencies, and running code. These are actions that would otherwise raise immediate suspicion outside a technical evaluation context.
Understanding this motivation helps explain both the persistence of these campaigns and the level of effort invested in making them believable.
How Fireblocks Identified and Disrupted a Coordinated Recruiting Impersonation Campaign
The campaign came to Fireblocks’ attention after multiple individuals reached out to customer-facing teams, HR, and other Fireblocks employees asking whether we were genuinely hiring for a specific new project called “Fireblocks Poker Platform”.
Those questions were escalated internally and quickly connected to our Security Research team, where they were analyzed alongside the technical artifacts and recruiting workflows involved.
Fireblocks then moved quickly to actively disrupt the campaign, starting with the impersonation surface itself.
Fireblocks security teams focused on identifying and validating the LinkedIn personas used in the outreach. As part of this analysis, Fireblocks identified multiple recruiter and hiring manager personas used repeatedly across the campaign:
| Persona Name | Role Claimed | Platform Used |
| Agnes Gonzales | Senior Technical Recruiter | Web3, Blockchain, and Crypto Hiring | Scaling Global Engineering & Product Teams | |
| Neira Cenuvieth | Talent Recruiter for the Blockchain Revolution | Connecting Web3 Innovators with World-Class Opportunities | |
| Sebas Puerto | Recruiter | Human Resources Partner | |
| José Enmanuel Sánchez Puche | Experienced Project Manager | Leading Successful Tech Projects | |
| Hedley Palmer | Director at Fireblocks | |
| Ana Maria Blandon | Servicio de atención al cliente en Fireblocks | |
| Brody Hunt | Web3 Team Leader | Driving Blockchain Innovation & Decentralized Solutions | Empowering Teams to Build the Future of Web3 | |
| Andrea Bosch Sánchez | Talent Acquisition Specialist | HR Analyst | |
| Lorena Rodríguez Cancio | HR & Learning Innovation Partner | |
| Jack Cummings | Web3 Talent Connector | |
| Indu Sharma | Finance Business Partner Analyst | |
| Roman Creed | HR Manager | Google ([email protected]) |
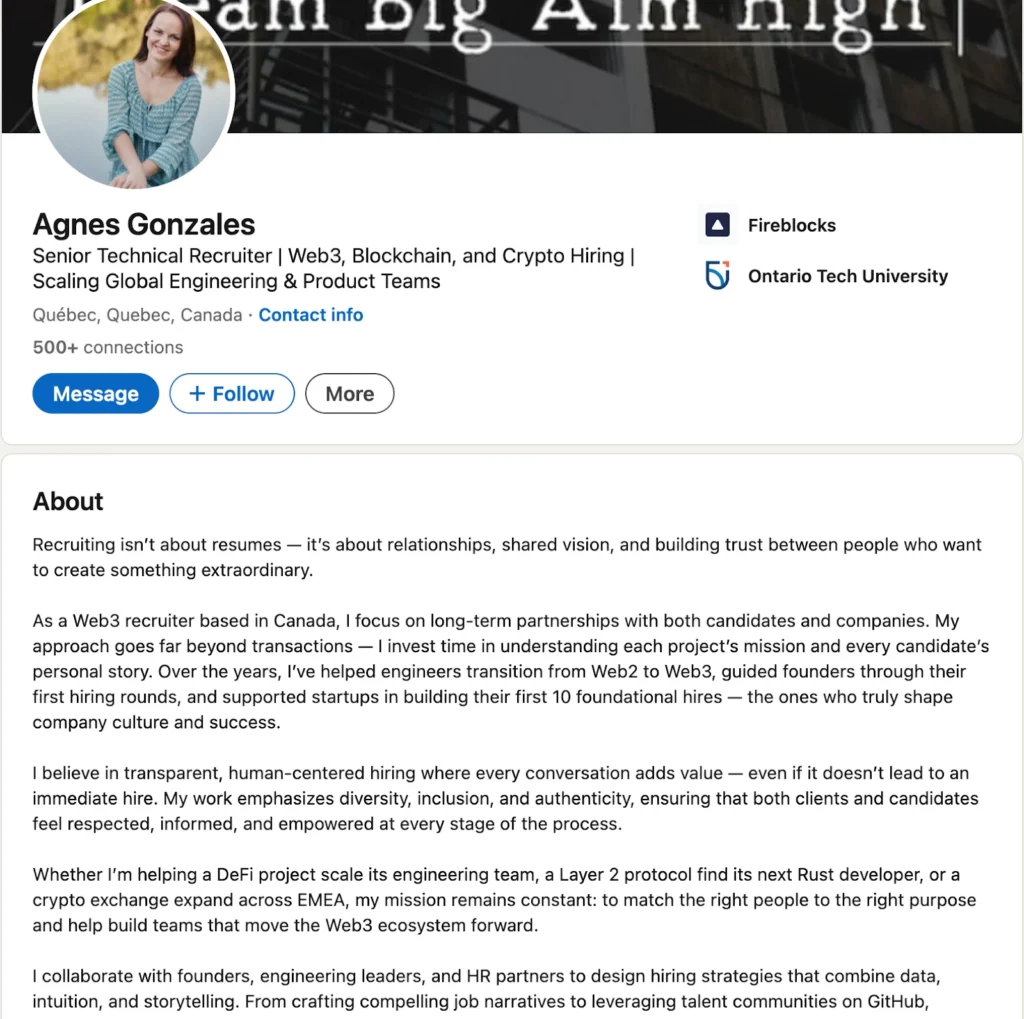
While the profiles appeared credible at first glance, closer review revealed consistent patterns that did not align with legitimate Fireblocks recruiting activity. In addition to the red flags noted above, we identified:
- Profiles that could not be verified through official Fireblocks recruiting channels, including the Fireblocks careers page, despite claiming to represent hiring roles at the company
- LinkedIn recruiter profiles with limited historical activity that suddenly became active, initiating outreach to multiple candidates within a short time frame
- Repeated reuse of language, role descriptions, and formatting across different recruiter personas, indicating coordinated profile creation rather than independent recruiting activity
- Profile content and imagery that appeared AI-generated or stock-based, combined with exaggerated, buzzword-heavy descriptions inconsistent with typical Fireblocks employee profiles
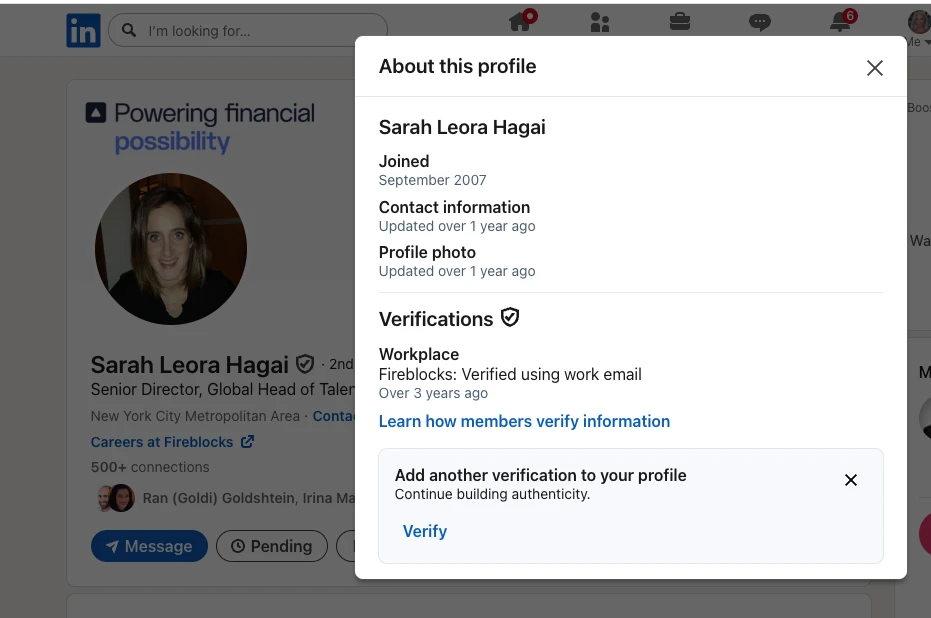
Once validated as impersonation, Fireblocks reported the recruiter profiles directly to LinkedIn and worked with the platform to support takedowns. In parallel, Fireblocks identified and reported the malicious repositories and supporting infrastructure used in the technical assignment stage, contributing to their removal.
Fireblocks also conducted targeted threat hunting to identify additional personas, repositories, and artifacts connected to the same campaign. We coordinated with intelligence partners and law enforcement to expand visibility into the activity and limit follow-on attempts.
Best-in-Class Operational Responses to Contagious Interview-Style Attacks
Recruiting impersonation campaigns like this one are not isolated incidents. They reflect a broader and persistent spear phishing and social engineering threat pattern that continues to evolve alongside normal business processes. As that evolution continues, the level of detail seen in cases like this is what makes social engineering in recruiting especially dangerous.
That sophistication showed up in very specific ways. The fake Figma project materials referenced our acquisition of Dynamic and reflected Fireblocks’ latest branding and infographics, both of which had only been announced weeks earlier. Seeing such up-to-date details embedded in a fraudulent project deck made clear that this was not generic phishing, but a campaign built by operators actively tracking their targets and updating lures in near real time, using real-world business situations to approach potential victims.
While attempts like these will continue, sharing concrete indicators, staying current on attacker techniques, and responding with discipline across teams materially changes the outcome. Awareness and execution are what turn a convincing campaign into a short-lived one.
Technical details about this campaign, including indicators of compromise (IOCs), are documented in our technical analysis.
Please note: All legitimate Fireblocks job openings are published on our official careers page, and any recruiting outreach should be cross-checked against those listings. Fireblocks recruiters and talent leaders use verified LinkedIn profiles authenticated with Fireblocks work email addresses.
FAQs
-
Are fake recruiter attacks in crypto similar to Contagious Interview by North Korean hackers?
Yes. This campaign uses similar techniques to past “Operation Dream Job” and “Contagious Interview” attacks. This includes fake recruiter outreach, social engineering, and developer-targeted malware. These tactics are consistent with threats attributed to North Korea-linked actors targeting digital asset firms. -
Why do phishing attacks often target developers and software engineers?
Developers frequently run external code as part of their workflow, making them ideal targets for phishing schemes. Attackers exploit this trusted behavior by delivering malware disguised as technical assessments or coding tests during fake recruitment efforts. -
Are recruiting impersonation scams only targeting crypto companies?
No, recruiting impersonation scams are not targeted to only crypto companies. While this campaign focused on crypto-related roles, the underlying techniques of impersonating recruiters and delivering malware, can affect any company that is hiring technical talent. This can include a variety of sectors from fintechs to enterprise SaaS. -
Is this a targeted attack against Fireblocks?
No. This campaign abused the trusted Fireblocks brand to target individuals in the digital assets space. We are publishing this research to disrupt their activities and raise global awareness.


